A) A man-in-the-middle attack
B) A brute-force attack
C) A connection-hijacking attackC.A connection-hijacking attack
D) A spoofing attackD.A spoofing attack
Correct Answer

verified
Correct Answer
verified
Multiple Choice
At what layer of the OSI/RM does a packet filter operate?
A) Layer 1
B) Layer 3
C) Layer 5
D) Layer 7
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?
A) Man-in-the-middle attack
B) Trojan
C) Denial of service
D) Zero-day attack
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
A) Application layer
B) Network layer
C) Session layer
D) Transport layer
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the following series of commands from a Linux system: iptables -A input -p icmp -s 0/0 -d 0/0 -j REJECT Which explanation best describes the impact of the resulting firewall ruleset?
A) Individuals on remote networks will no longer be able to use SSH to control internal network resources.
B) Internal hosts will not be able to ping each other using ICMP.
C) Stateful multi-layer inspection has been enabled.
D) Individuals on remote networks will not be able to use ping to troubleshoot connections.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following errors most commonly occurs when responding to a security breach?
A) Shutting down network access using the firewall, rather than the network router
B) Adhering to the company policy rather than determining actions based on the IT manager's input
C) Making snap judgments based on emotions, as opposed to company policy
D) Taking too much time to document the attack
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
A) Authentication databases, including directory servers
B) Intrusion detection systems, especially those placed on sensitive networks
C) Log files on firewall systems
D) Firewall settings for desktop systems
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following can help you authoritatively trace a network flooding attack?
A) Your ISP
B) Firewall logs
C) Router logs
D) Ping
Correct Answer

verified
A
Correct Answer
verified
Multiple Choice
Which of the following is a primary weakness of asymmetric-key encryption?
A) It is slow because it requires extensive calculations by the computer.
B) It can lead to the corruption of encrypted data during network transfer.
C) It is reliant on the Secure Sockets Layer (SSL) standard, which has been compromised.
D) It is difficult to transfer any portion of an asymmetric key securely.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
At the beginning of an IPsec session, which activity occurs during the Internet Key Exchange (IKE) ?
A) Determining the number of security associations
B) Negotiating the authentication method
C) Determining the network identification number
D) Negotiating the version of IP to be used
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which algorithm can use a 128-bit key, and has been adopted as a standard by various governments and corporations?
A) MARS
B) RC2
C) Advanced Encryption Standard (AES)
D) International Data Encryption Algorithm (IDEA)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
A) Updating the company vulnerability scanner and conducting a new scan
B) Adding a buffer overflow rule to the intrusion detection system
C) Reconfiguring the firewall
D) Installing a system update
Correct Answer

verified
D
Correct Answer
verified
Multiple Choice
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
A) Auditing the firewall
B) Implementing non-repudiation
C) Logging users
D) Classifying systems
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following details should be included in documentation of an attack?
A) An overview of the security policy and suggestions for the next response plan
B) Estimates of how much the attack cost the company, and a list of the applications used by the attacker
C) The time and date of the attack, and the names of employees who were contacted during the response
D) The network resources involved in the attack, and recommendations for thwarting future attacks
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is a primary auditing activity?
A) Encrypting data files
B) Changing login accounts
C) Checking log files
D) Configuring the firewall
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which choice lists typical firewall functions?
A) Creating a VLAN and configuring the intrusion-detection system
B) Issuing alerts and limiting host access
C) Logging traffic and creating a choke point
D) Implementing the security policy and scanning the internal network
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Consider the following image of a packet capture: 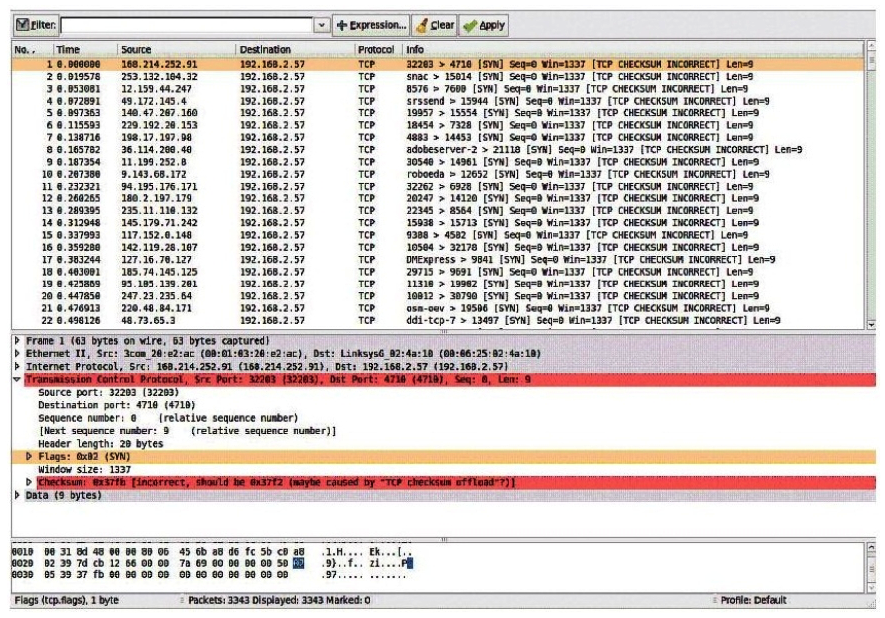 This packet capture has recorded two types of attacks. Which choice lists both attack types?
This packet capture has recorded two types of attacks. Which choice lists both attack types?
A) A dictionary attack and a worm-based attackA.A dictionary attack and a worm-based attack
B) A syn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C) A worm attack and a botnet attack C.A worm attack and a botnet attack
D) A SQL injection attack and a virus attackD.A SQL injection attack and a virus attack
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have implemented a version of the Kerberos protocol for your network. What service does Kerberos primarily offer?
A) Authentication
B) Encryption
C) Non-repudiation
D) Data integrity
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
A) The extra hard disk space required to store the database of checksums
B) The amount of memory remaining now that the checksum-based application is running
C) The possibility of a buffer overflow attack leading to a security breach
D) The security of the checksum database on a read-only media format
Correct Answer

verified
D
Correct Answer
verified
Multiple Choice
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
A) Configuring network intrusion-detection software to monitor end user activity
B) Conducting a training session at the time of hire
C) Reconfiguring the network firewall
D) Assembling a team of security professionals to monitor the network
Correct Answer

verified
Correct Answer
verified
Showing 1 - 20 of 48
Related Exams