A) PIN Number and Birth Date
B) Username and Password
C) Digital Certificate and Hardware Token
D) Fingerprint and Smartcard ID
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Allen and Greg, after investing in their startup company called Zamtac Ltd., developed a new web application for their company. Before hosting the application, they want to test the robustness and immunity of the developed web application against attacks like buffer overflow, DOS, XSS, and SQL injection. What is the type of the web application security test Allen and Greg should perform?
A) Web fuzzing
B) Web crawling
C) Web spidering
D) Web mirroring
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How can a policy help improve an employee's security awareness?
A) By implementing written security procedures, enabling employee security training, and promoting the benefits of security
B) By using informal networks of communication, establishing secret passing procedures, and immediately terminating employees
C) By sharing security secrets with employees, enabling employees to share secrets, and establishing a consultative help line
D) By decreasing an employee's vacation time, addressing ad-hoc employment clauses, and ensuring that managers know employee strengths
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of security document is written with specific step-by-step details?
A) Process
B) Procedure
C) Policy
D) Paradigm
Correct Answer

verified
Correct Answer
verified
Multiple Choice
SecGlobal Corporation hired Michael, a penetration tester. Management asked Michael to perform cloud penetration testing on the company's cloud infrastructure. As a part of his task, he started checking all the agreements with cloud service provider and came to a conclusion that it is not possible to perform penetration testing on the cloud services that are being used by the organization due to the level of responsibilities between company and the Cloud Service Provider (CSP) . Identify the type of cloud service deployed by the organization?
A) Platform as a service (PaaS)
B) Software as a service (SaaS)
C) Anything as a service (XaaS)
D) Infrastructure as a service (IaaS)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have several plain-text firewall logs that you must review to evaluate network traffic. You know that in order to do fast, efficient searches of the logs you must use regular expressions. Which command-line utility are you most likely to use?
A) MS Excel
B) Notepad
C) Grep
D) Relational Database
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
A) Threaten to publish the penetration test results if not paid.
B) Follow proper legal procedures against the company to request payment.
C) Tell other customers of the financial problems with payments from this company.
D) Exploit some of the vulnerabilities found on the company webserver to deface it.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
A) Packet filtering firewall
B) Application-level firewall
C) Circuit-level gateway firewall
D) Stateful multilayer inspection firewall
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Adam is working as a senior penetration tester at Eon Tech Services Ltd. The company asked him to perform penetration testing on their database. The company informs Adam they use Microsoft SQL Server. As a part of the penetration testing, Adam wants to know the complete information about the company's database. He uses the Nmap tool to get the information. Which of the following Nmap commands will Adam use to get the information?
A) nmap -p2051 --script ms-sql-info
B) nmap -p1801 --script ms-sql-info
C) nmap -p1443 --script ms-sql-info
D) nmap -p1521 --script ms-sql-info
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which security strategy requires using several, varying methods to protect IT systems against attacks?
A) Defense in depth
B) Three-way handshake
C) Covert channels
D) Exponential backoff algorithm
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following tasks is done after submitting the final pen testing report?
A) Kick-off meeting
B) System patching and hardening
C) Exploiting vulnerabilities
D) Mission briefing
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which results will be returned with the following Google search query? site:target.com -site:Marketing.target.com accounting
A) Results matching all words in the query
B) Results matching "accounting" in domain target.com but not on the site Marketing.target.com
C) Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting
D) Results for matches on target.com and Marketing.target.com that include the word "accounting"
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are enumerating a target system. Which of the following PortQry commands will give a result similar to the screenshot below: 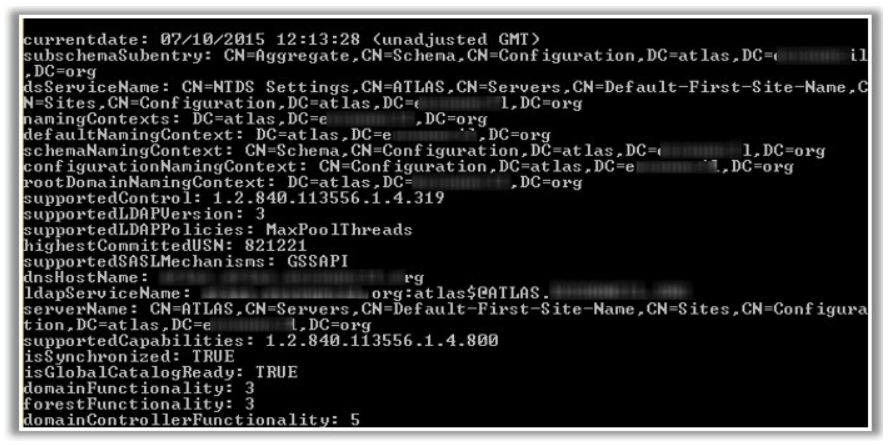
A) portqry -n myserver -p udp -e 389
B) portqry -n myserver -p udp -e 123
C) portqry -n myserver -p TCP -e 389
D) portqry -n myserver -p TCP -e 123
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is an example of IP spoofing?
A) SQL injections
B) Man-in-the-middle
C) Cross-site scripting
D) ARP poisoning
Correct Answer

verified
Correct Answer
verified
Multiple Choice
SOAP services use which technology to format information?
A) SATA
B) PCI
C) XML
D) ISDN
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Stuart is a database penetration tester working with Regional Server Technologies. He was asked by the company to identify the vulnerabilities in its SQL database. Stuart wanted to perform a SQL penetration by passing some SQL commands through a web application for execution and succeeded with a command using a wildcard attribute indicator. Which of the following strings is a wildcard attribute indicator?
A) Param1=foo&Param2=bar
B) %
C) @variable
D) @@variable
Correct Answer

verified
Correct Answer
verified
Multiple Choice
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
A) Hping
B) Traceroute
C) TCP ping
D) Broadcast ping
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following scanning tools is specifically designed to find potential exploits in Microsoft Windows products?
A) Microsoft Security Baseline Analyzer
B) Retina
C) Core Impact
D) Microsoft Baseline Security Analyzer
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A month ago, Jason, a software developer at a reputed IT firm was surfing through his company's website. He was visiting random pages of the company's website and came to find confidential information about the company was posted on one of the web pages. Jason forgot to report the issue. Jason contacted John, another member of the Security Team, and discussed the issue. John visited the page but found nothing wrong. What should John do to see past versions and pages of a website that Jason saw one month back?
A) John should use SmartWhois to recover the old pages of the website
B) John should recover cashed pages of the website from Google search engine cache
C) John should run the Web Data Extractor tool to recover the old data
D) John can go to Archive.org to see past versions of the company website
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which tool can be used to silently copy files from USB devices?
A) USB Grabber
B) USB Dumper
C) USB Sniffer
D) USB Snoopy
Correct Answer

verified
Correct Answer
verified
Showing 181 - 200 of 317
Related Exams