A) Change the WLAN reserved bandwidth for WebEx
B) Create an AVC profile for WebEx
C) Create an ACL for WebEx
D) Change the AVC application WebEx-app-sharing to mark
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer is implementing Cisco Identity-Based Networking on a Cisco AireOS controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy. What is the resulting ACL when a Human Resources user connects?
A) HR_ACL appended with BASE_ACL
B) HR_ACL only
C) BASE_ACL appended with HR_ACL
D) BASE_ACL only
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer is performing a Cisco Hyperlocation accuracy test and executes the cmxloc start command on Cisco CMX. Which two parameters are relevant? (Choose two.)
A) X, Y real location
B) client description
C) AP name
D) client MAC address
E) WLC IP address
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A) Social Connect
B) Client Connect
C) Visitor Connect
D) Guest Connect
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Branch wireless users report that they can no longer access services from head office but can access services locally at the site. New wireless users can associate to the wireless while the WAN is down. Which three elements (Cisco FlexConnect state, operation mode, and authentication method) are seen in this scenario? (Choose three.)
A) authentication-local/switch-local
B) WPA2 personal
C) authentication-central/switch-central
D) lightweight mode
E) standalone mode
F) WEB authentication
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer is setting up a WLAN to work with a Cisco ISE as the AAA server. The company policy requires that all users be denied access to any resources until they pass the validation. Which component must be configured to achieve this stipulation?
A) WPA2 passkey
B) AAA override
C) CPU ACL
D) preauthentication ACL
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A) open authentication
B) high RSSI
C) foreign SSID
D) accepts clients
E) low RSSI
F) distant location
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer is tuning RRM parameters to improve client connectivity. Which channel band results in the best 802.11n client compatibility?
A) UNII-2
B) UNII-2e
C) UNII-3
D) UNII
E) UNII-1
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer must deploy FlexConnect APs to a site that typically has 300 ms latency to the WLC. Which typical operating mode must the engineer plan on for normal operations?
A) local authentication, local switching
B) central authentication, central switching
C) central authentication, local switching
D) connected mode
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
A) Policy Profile
B) AP Join Profile
C) Flex Profile
D) RF Profile
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
A) multicast
B) static IP
C) fast roaming
D) mDNS
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A corporation is spread across different countries and uses MPLS to connect the offices. The senior management wants to utilize the wireless network for all the employees. To ensure strong connectivity and minimize delays, an engineer needs to control the amount of traffic that is traversing between the APs and the central WLC. Which configuration should be used to accomplish this goal?
A) FlexConnect mode with central switching enabled
B) FlexConnect mode with central authentication
C) FlexConnect mode with OfficeExtend enabled
D) FlexConnect mode with local authentication
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is an important consideration when implementing a dual SSID design for BYOD?
A) After using the provisioning SSID, an ACL that used to make the client switch SSIDs forces the user to associate and traverse the network by MAC filtering.
B) If multiple WLCs are used, the WLAN IDs must be exact for the clients to be provisioned and traverse the network correctly.
C) SSIDs for this setup must be configured with NAC State-RADIUS NAC for the clients to authenticate with Cisco ISE, or with NAC State-ISE NAC for Cisco ISE to associate the client.
D) One SSID is for provisioning and the other SSID is for gaining access to the network. The use of an ACL should not be enforced to make the client connect to the REAL SSID after provisioning.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
A) The last device is removed and the newly added device is updated as active device.
B) The registration is allowed, but only one device is connected at any given time.
C) All devices are allowed on the network simultaneously.
D) Purge time dictates how long a device is registered to the portal.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.) 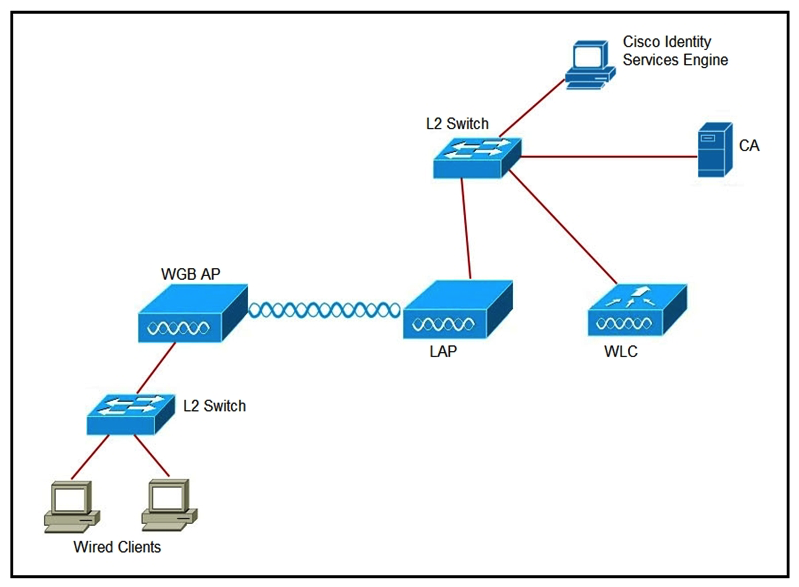
A) Configure the certificate, WLAN, and radio interface on WGB.
B) Configure the certificate on the WLC.
C) Configure WLAN to authenticate using ISE.
D) Configure the access point with the root certificate from ISE.
E) Configure WGB as a network device in ISE.
F) Configure a policy on ISE to allow devices to connect that validate the certificate.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations? 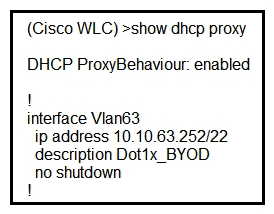
A) Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE configuration must be fixed.
B) Disable DHCP proxy on the Cisco WLC.
C) Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers. Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers.
D) Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the VLAN interface to point to the two ISE servers.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the default NMSP echo interval between Cisco MSE and a Wireless LAN Controller?
A) 10 seconds
B) 15 seconds
C) 30 seconds
D) 60 seconds
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which network is connected by default when connecting to the unused Ethernet port of a MAP?
A) the native VLAN that the MAP is connected to
B) the VLAN that is associated with WLAN number 1 in the WLC
C) the native VLAN that the WLC is connected to
D) the VLAN that is associated with the SSID that the MAPs are communicating on
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The Cisco Hyperlocation detection threshold is currently set to -50 dBm. After reviewing the wireless user location, discrepancies have been noticed. To improve the Cisco Hyperlocation accuracy, an engineer attempts to change the detection threshold to -100 dBm. However, the Cisco Catalyst 9800 Series Wireless Controller does not allow this change to be applied. What actions should be taken to resolve this issue?
A) Disable Cisco Hyperlocation, change the Cisco Hyperlocation detection threshold, and then enable it.
B) Create a new profile on Cisco CMX with the new Cisco Hyperlocation detection range, and apply it on the WLAN.
C) Place the APs to monitor mode, shutdown the radios, and then change Cisco Hyperlocation detection threshold.
D) Shutdown all radios on the controller, change the Cisco Hyperlocation detection range, and enable the radios again.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
A) network policy server
B) RADIUS
C) TACACS+
D) LDAP
Correct Answer

verified
Correct Answer
verified
Showing 81 - 100 of 101
Related Exams